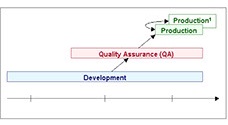
It is common practise that Development and Test environments for business application systems most times would also hold sensitive customer data that is used to develop, simulate, and test the application code logic. This implies that these test non-production environments also need to be secured in the same way as the Production IT Environment.
The Open Web Application Security Project, or OWASP an international non-profit organization dedicated to web application security has identified two of the Top 10 security vulnerabilities as follows:
-
Broken Authentication: Relies on using stolen, misconfigured, or otherwise vulnerable login data to gain access to a system.
-
Broken Access Control: Relies on failures in user and role permission configuration to enable unauthorized access.
There is a plethora of cybersecurity tools in the market that can assist in deterring or preventing unauthorised access to a server, an IT network, software application and computer systems overall that will host a test or development IT Environment.
Another effective approach to tackle the two vulnerabilities mentioned above will be to build and deploy proactive automation tools, utilities, bots that provide a high degree of vigilance in the following manner.
-
Automation tools or features that can track, analyse & report what users have logged into a system, what they are doing, in the process identify patterns/trends that will highlight any anomalies or unauthorised access to the Host Server of a test or development environment.
-
Since computer hacking to a point is a crime of opportunity, automation tools that will instantly highlight any repeated attempts to gain unauthorised access to the Host Server of your Test Environment are highly desirable.
-
Instant, real time, continuous view of all activity on your server can certainly assist in spotting rogue, spurious or illegal activity on the Host Server of a test or development IT environment.